
I dont know much about Tor network, I just experienced it once.
Very first thing it is not a P2P network; its an Overlay network kind of thing.
It has some important parts
- Rendezvous points(where nodes make introduction requests and responsible to create circuit)
- Onion routers(for taking routing decisions)
- Relays(servers which provides anonymity to Tor clients)
- Directory servers(which redistribute relay(server) lists as directories to clients)
Tor clients obtain anonymity by building circuits of usually three relays that redirect their communication before exiting to the real Internet. All messages along the circuits are encrypted multiple times so that neither participant can tell where the circuit begins and where it ends.The result of this redirection is that nobody can link the clients’ IP addresses to the data contents. All data is sent in fixed size cells. By compromising starting and end point information can be revealed.
How Tor provides anonymity?
To clarify it I have taken some pics created by Gregory Norcie

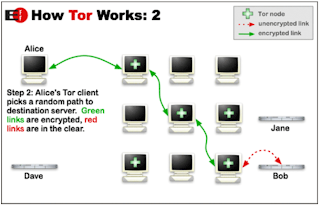


Tor also provide integrity checking with perfect(pseudo) forward secrecy.
Remember:
# Not secure against end to end attacks
# Not steganographic
Note: I may include more further.

1 comment:
Above figure seems to be onion
thats why name onion routing
The second generation Onion Router
Interesting article geek dude carry on
Post a Comment