Monday, May 31, 2010
Create a disposable email address and fight against Spams
1.
http://www.jetable.org/en/index
follow the link.
2.
Give your legitimate email address to jetable.org
3.
Specify the time period in hours, days or moth as per your requirement.
4.
And click on the create button.
5.
Copy the created email address and give it to anywhere on net and anonymize your email address.
:)
Some other mail providers are also available which provide more or less same facility:
# 10minutemail.com
It gives you a fake email address only for 10 minutes by default, if you want more 10 minute it can give the time but not more than that.
# 12hourmail.com
It give you an email address for 12 hours as the name suggest, after 12 hour all the mails will be deleted from the Inbox.
# emailinator.com
It is also a free disposable e-mail address service with no registration required.
# www.guerrillamail.com
This website also provides you the same email service which expire after 15 Minutes.
# mailcatch.com/
# www.tempinbox.com/
# spamfree24.org
There may be many more but definitely for the same purpose. Use and enjoy :)
Sunday, May 30, 2010
LITIGATION THAT IS COMMONLY CONCERNED WITH EMAIL
use and misuse of email in many different ways:
1. The civil and criminal offences of harassment under the Protection from Harassment Act involve a course of conduct that causes distress. The sending of harassing emails can amount to a course of conduct.
2. A libel occurs where a person makes a statement to another about a third party that causes the other to think less of the third party. Obviously, emails can be used to communicate libelous statements.
3. The Malicious Communications Act criminalizes the sending of ‘hate mail’, which includes the sending of hate email.
4. person can breach their duty of confidence in confidential email through the sending of an email to another person.
5. Emails can be used to send infringing copies of copyright protected materials.
6. Unlawfully obtaining personal data contained in emails is a criminal offence under the Data Protection Act.
7. Using a computer without permission to gain access to emails is a hacking offence under the Computer Misuse Act.
8. Disclosing emails without permission or lawful authority can infringe a person’s right to privacy under the Human Rights Act.
9. Intercepting emails without lawful authority is a criminal offence under the Regulation of Investigatory Powers Act.
10. Distance contracting by email where the seller neglects to provide core information about themselves and their business is unlawful under the Consumer Protection Distance Selling Regulations.
11. The sending of spam emails is unlawful under the Privacy and Electronic Communications(EC
Directive) Regulations. Within a fractured environment the organization carries an unascertained risk of breaching the law in literally thousands of different ways.
Friday, May 28, 2010
Wednesday, May 26, 2010
Command to set proxy
$export http_proxy=http://mnnit:mnnit@172.31.100.29:3128
[KG]
Monday, May 24, 2010
Email Archiving and Email Compliance

Email Archiving is the management of exponentially growing email archives onto a different storage media, this might be to a local drive, into a .pst file, printing off the email onto paper and sticking it in the client files, or possibly moving the email onto alternative storage media. May be this is not good enough! Organizations also looking at email compliance which requires for the emails to be kept for compliance and legislative purposes in a central repository. This central repository should not be able to be tampered with any form, any access Administrator/Supervisory Access to this central repository should form part of a formal procedure with auditing to comply with the privacy legislation, notably the Data Protection Act (DPA) and Human Rights Legislation.
Saturday, May 22, 2010
TOR

I dont know much about Tor network, I just experienced it once.
Very first thing it is not a P2P network; its an Overlay network kind of thing.
It has some important parts
- Rendezvous points(where nodes make introduction requests and responsible to create circuit)
- Onion routers(for taking routing decisions)
- Relays(servers which provides anonymity to Tor clients)
- Directory servers(which redistribute relay(server) lists as directories to clients)
Tor clients obtain anonymity by building circuits of usually three relays that redirect their communication before exiting to the real Internet. All messages along the circuits are encrypted multiple times so that neither participant can tell where the circuit begins and where it ends.The result of this redirection is that nobody can link the clients’ IP addresses to the data contents. All data is sent in fixed size cells. By compromising starting and end point information can be revealed.
How Tor provides anonymity?
To clarify it I have taken some pics created by Gregory Norcie

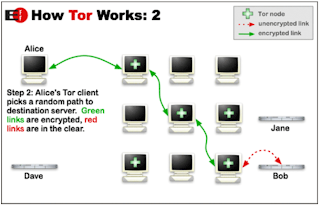


Tor also provide integrity checking with perfect(pseudo) forward secrecy.
Remember:
# Not secure against end to end attacks
# Not steganographic
Note: I may include more further.
Few steps to speed up Firefox than Google Chrome

Google Chrome has now eclipsed Mozilla Firefox in the speed category. However, I still use Firefox as my main web browser because it is still better than Chrome in certain areas.
But you need to try a few tweaks that significantly improve the speed of Firefox making it a little bit snappier than the latest version of Google Chrome when loading webpages.
Here are some of the things that I did that helps make Firefox somewhat faster than Chrome:
1. Type about:config into the Firefox URL/address bar and hit ENTER. You will be warned that you might void your warranty if you change some advanced settings, but just go on and trust me :-)
2. Inside the Firefox configuration page, scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
Set their values to “true” by double-clicking each one of them.
3. Next up, find this entry:
network.http.pipelining.maxrequests
Double-click and set the value to 8.
4. Right-click anywhere inside the config page and select New --> Integer. Name it nglayout.initialpaint.delay and set the value to “0″.
5. Right-click anywhere inside the config page and select New --> Integer. Name it content.notify.interval and set the value to “500000″.
6. Right-click anywhere inside the config page and select New --> Boolean. Name it content.notify.ontimer and set the value to “true″.
7. Right-click anywhere inside the config page and select New --> Integer. Name it content.switch.threshold and set the value to “250000″.
8. Right-click anywhere inside the config page and select New --> Boolean. Name it content.interrupt.parsing and set the value to “false″.
That's about it. You should be able to notice the speed improvement immediately after applying the above tweaks.
Disabling Firefox addons that you don't use often, blocking flash content, and using a lightweight theme will also help speed up Firefox.
Thursday, May 20, 2010
Wednesday, May 19, 2010
WEB BROWSERS LEAVE 'FINGERPRINTS' BEHIND AS YOU SURF THE NET

Foundation (EFF) has found that an overwhelming majority of
web browsers have unique signatures -- creating
identifiable "fingerprints" that could be used to track you
as you surf the Internet.
EFF Research Shows More Than 8 in 10 Browsers Have Unique,
Trackable Signatures.
The findings were the result of an experiment EFF conducted
with volunteers who visited http://panopticlick.eff.org/.
The website anonymously logged the configuration and
version information from each participant's operating
system, browser, and browser plug-ins -- information that
websites routinely access each time you visit -- and
compared that information to a database of configurations
collected from almost a million other visitors. EFF found
that 84% of the configuration combinations were unique and
identifiable, creating unique and identifiable browser
"fingerprints." Browsers with Adobe Flash or Java plug-ins
installed were 94% unique and trackable.
https://panopticlick.eff.org/browser-uniqueness.pdf
Friday, May 14, 2010
 If you feel any kind of attack on your system/server:
If you feel any kind of attack on your system/server:Contact the Computer Emergency Response Team (CERT) at cert@cert.org about the attack so that they can track the incidents. The CERT Coordination Center charter is to work with the Internet community to facilitate its response to computer security events involving Internet hosts, to take proactive steps to raise the community's awareness of computer security issues, and to conduct research targeted at improving the security of existing systems.
World Cyber War

The United States is losing enough data in cyber attacks in another words U. S. not winning cyber war.
More than 100 foreign spy agencies were working to gain access to U.S. computer systems, as were criminal organizations, said James Miller, principal deputy under secretary of defense for policy.
Terrorist groups also had cyber attack capabilities.
"Our systems are probed thousands of times a day and scanned millions of times a day," Miller told a forum sponsored by Ogilvy Washington, a public relations compa
He said the evolving cyber threat had "outpaced our ability to defend against it."
"We are experiencing damaging penetrations -- damaging in the sense of loss of information. And we don't fully understand our vulnerabilities," Miller said.
http://itmanagement.earthweb.com/features/article.php/3881921/US-Not-Winning-Cyber-War.htm
"Avalanche's(Single Gang Dominated Two-third Phishing Attacks in 2009)
Researchers said the Avalanche group is by far the world's most prolific phishing operation because its members managed to perfect a two-pronged system that simultaneously deploys mass-producing phishing sites while also distributing malware that gives the crooks even more tools to pull off their scams.
"The data shows that the anti-phishing community -- including the target institutions, security responders, and domain name registries and registrars -- got very good at identifying and shutting down Avalanche's attacks on a day-to-day basis," said Rod Rasmussen, founder and CTO of Internet Identity and a co-author of the report.



